This blog post shows the analysis of a malware of the PyRation family by Tomas Nieponice as part of a 3-week winter cybersecurity internship at the Stratosphere Laboratory. The internship was done under the supervision of Assist. prof. Sebastian Garcia, PhD.
Studying Cybercrime is Fun! An Overview of Five Years of Research Surrounding the Geost Botnet
Deep Dive into an Obfuscation-as-a-Service for Android Malware
While confined in our homes studying the interactions of individuals involved in the spread of the Android banking Trojan botnet (known as Geost), we encountered a unique opportunity: investigate an automated obfuscation-as-a-service platform for Android malware authors.
Indeed, in a leaked chat log that involved Geost botnet operators, two individuals talked about an obfuscation service used to “protect” their malicious Android Applications (APKs) from being detected by antivirus engines. We visited the website related to the “protection” service (protection from antivirus engines -so basically obfuscation), which raised a lot of questions: How does this obfuscation service work? Is it automated? Does it really obfuscate applications well enough to avoid malicious applications being detected? How well is the service known in the underground community?
RHOMBUS: a new IoT Malware
Hexa Payload Decoder Tool: A Tool To Automatically Extract and Decode Hex Data in C&C Servers
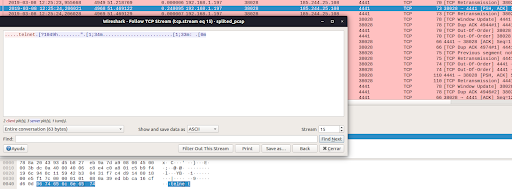
In this blog post we introduce the “Hexa Payload Decoder Tool”, a tool that is able to process a pcap file and return any decoded characters translated to English. This tool was developed to assist the network security analyst when working and interpreting data sent and received by command and control servers used by malware.
IoT Malware Analysis Series. An IoT malware dropper with custom C&C channel exploiting HNAP
What do we know about Quasar RAT? A review.
What do we know about NanoCore RAT? A review.
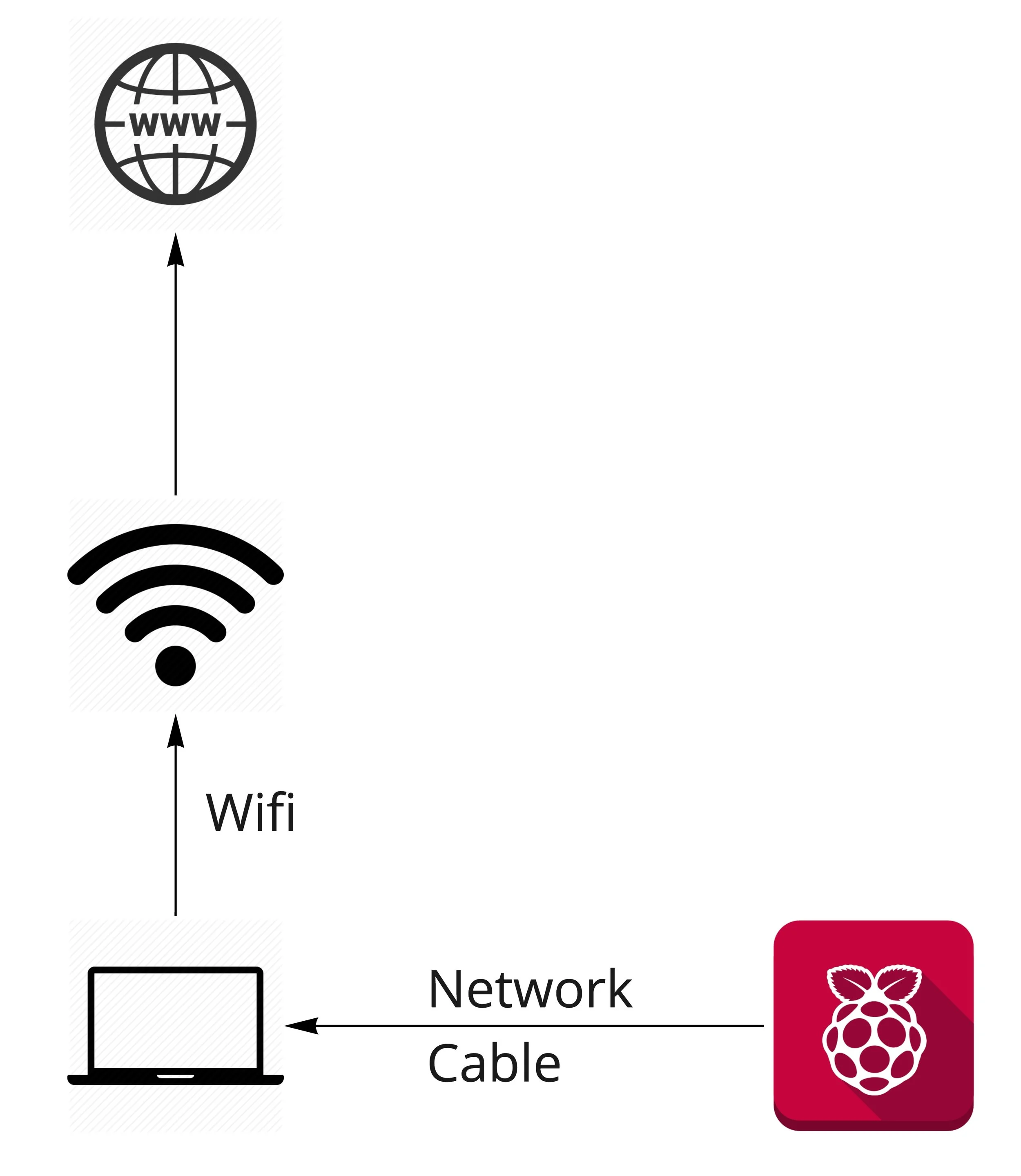
How to Create a Small Lab at Home with a Raspberry Pi to execute Malware
ANALISIS OF CTU-MALWARE-CAPTURE-1 (ZBOT.OOWO)
CTU-MALWARE-CAPTURE-1 (ZBOT.OOWO)
This capture was done between Thu Sep 5 15:40:07 CEST 2013 and Tue Oct 1 13:38:29 CEST 2013, having a total of 25 days and 21 hours. It corresponds to a binary with the MD5 46b3df3eaf1312f80788abd43343a9d2 of and that was classified by Kaspersky in VirusTotal as Trojan-Spy.Win32.Zbot.oowo. However we are not sure of the name.