We started working with UptimeRobot in our IoT lab, and it was like suddenly someone turned on the light.
The prevalence of DNS over HTTPS By Karel Hynek
White Paper: Current State of IPv6 Security in IoT
This white paper explores what is the current state of IPv6 security in IoT, what is the global growth of IPv6 and how does this growth look like in a real network. If IPv6 is already being used, are attackers already attacking using this protocol? Is there already malware capable of attacking on IPv6? Read through as we aim to answer these questions.
Data Exfiltration via IPv6
Within the Aposemat Team, we’ve been working on testing the capabilities of IPv6 and how malware could take advantage of it. One of the topics we explored was exfiltration of data via the IPv6 protocol. In this blog post we will share our study into this topic.
CVE search tool
CVEs, or Common Vulnerabilities and Exposures, are IDs used to reference know vulnerabilities. These provide a description and public information provided by the parties involved in the disclosure of the vulnerability or exposure and are often used by researchers to act upon the disclosed information. While working on collecting information about specific CVEs in a simple form we came up with an small piece of code that will make that work much simpler and fast.
Dark Nexus: the old, the new and the ugly
RHOMBUS: a new IoT Malware
IoT-23 In Depth: CTU-IoT-Malware-Capture-1-1
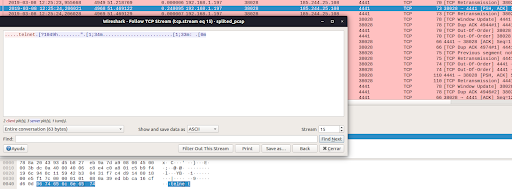
This post is a continuation of the IoT-23 In Depth series based on the IoT-23 Dataset, the first dataset of malicious and benign IoT network traffic, that consists of 23 scenarios. In this blog post we provide an analysis of Scenario 9, CTU-IoT-Malware-Capture-60-1. This malware sample is called Hide-and-Seek. This variant is an IoT malware family capable of different types of DDoS attacks, exploits vulnerabilities in other devices, such as routers and wireless cameras, and to brute force the Telnet service across the Internet to expand its botnet. This malware makes use of the custom peer-to-peer (P2P) protocol to transfer data.
IoT-23 In Depth: CTU-IoT-Malware-Capture-60-1
This post is a continuation of the IoT-23 In Depth series based on the IoT-23 Dataset, the first dataset of malicious and benign IoT network traffic, that consists of 23 scenarios [1]. In this blog post we provide an analysis of Scenario 9 [2], CTU-IoT-Malware-Capture-60-1. This malware sample is called Gafgyt. This variant is an IoT malware family capable of different types of DDoS attacks and exploits vulnerabilities in other devices, such as routers, to expand its botnet which has been seen attacking gaming servers [3].
Swiss Cyber Security Days: Conference Wrap-Up
The Swiss Cyber Security Days are a two-day event in Fribourg, Switzerland. This event brought together Cyber security researchers, consultants from technology, business, politics and the general public interested in cybersecurity from all over the world.
At the second edition of the Swiss Cyber Security Days our researcher Maria Jose Erquiaga presented the work of the Aposemat laboratory in the talk: “The Truth is out there: Hunting malware from an IoT laboratory”.
IoT-23 In Depth: CTU-IoT-Malware-Capture-8-1
This post is a continuation of the IoT-23 In Depth series based on the IoT-23 Dataset, the first dataset of malicious and benign IoT network traffic, that consists of 23 scenarios [1]. In this blog post we provide an analysis of Scenario 13 [2], CTU-IoT-Malware-Capture-8-1. This malware sample is called Hakai and it’s a variant of Linux.Mirai/Gafgyt. Mirai is an IoT malware family capable of different types of DDoS attacks, telnet brute force attacks and it uses different sets of exploits to infect other devices, such as routers.
IoT-23 In Depth: CTU-IoT-Malware-Capture-3-1
This post is a continuation of the IoT-23 In Depth series based on the IoT-23 Dataset, the first dataset of malicious and benign IoT network traffic, that consists of 23 scenarios [1]. In this blog post we show an analysis of Scenario 19 [2], CTU-IoT-Malware-Capture-3-1. This malware sample is called Muhstik and it’s a variant of the STD/Tsunami bot. The STD/Tsunami bot is an IoT malware capable of different types of DDoS attacks and it uses the IRC protocol to communicate with its C&C server.
Zeek: New IRC Feature Extractor Package
Zeek Package IRC Feature Extractor extends the functionality of Zeek network analysis framework. We create IRC Feature Extractor Zeek Package to automatically recognize IRC communication in a packet capture (pcap) file and to extract features from it. The goal for the feature extraction is to describe an individual IRC communications that occur in the pcap file as accurately as possible.
IoT-23 In Depth: CTU-IoT-Malware-Capture-9-1
A couple of weeks ago, we released the IoT-23 Dataset, the first dataset of malicious and benign IoT network traffic, that consists of 23 scenarios. In this blog post we provide an analysis of Scenario 18, CTU-IoT-Malware-Capture-9-1. This malware sample is Hajime. We analysed the binary sample and the network traffic of this scenario.
Aposemat IoT-23: A Labeled Dataset With Malicious And Benign IoT Network Traffic
Aposemat IoT Honeypots: 2019 In Review
Attacker IP Prioritizer Program
he Attacker IP Prioritization (AIP) algorithm was created in order to sort the huge amount of attacker’s IP addresses to help block them using a blacklist. In the Aposemat project we started a research line called “Polonium in my IoTea” were we are trying to investigate the relationship between organized cyber crime groups (e.g. FancyBear) and their use of IoT devices. In this investigation we needed to analyze thousands of IP addresses attacking our honeypots and quickly decide which ones were the most dangerous.The idea of the AIP algorithm was born from the need to sort the IP addresses of the attackers from a statistical point of view, and then compare those rated IPs to our more technical and in-depth attack research to find out if an IP is really part of an important attacker group or not.
Notes From The Lab: Sudden Increase of Traffic to Port 445
Today @VessOnSecurity tweeted that they have seen an increase on the number of SMB attacks in their honeypot (See Figure 1). We checked our telemetry and indeed we saw an increase on the incoming traffic to our honeypots on port 445. We will describe in this blog post the observations from our telemetry.
Hexa Payload Decoder Tool: A Tool To Automatically Extract and Decode Hex Data in C&C Servers
In this blog post we introduce the “Hexa Payload Decoder Tool”, a tool that is able to process a pcap file and return any decoded characters translated to English. This tool was developed to assist the network security analyst when working and interpreting data sent and received by command and control servers used by malware.