This blog post describes the analysis of a malware sample that was executed in a RapsberryPi from our IoT laboratory. The SHA256 of the sample that we executed in our laboratory is: d8040a64b88b4a738d333015ddd93a27187abb7584412df56633a7e7d12127f4.
IoT Malware Analysis Series. An IoT malware dropper with custom C&C channel exploiting HNAP
Analysis of an IRC based Botnet
This blogpost aims to give an insight of an IRCBased botnet describing the network behavior and showing the analysis of the C&C. By analyzing this botnet network traffic it was possible to identify the botmasters using an IRC channel and observe not only the conversation between them but also the orders they give to the bot.
IoT Honeypot Traffic Analysis Series. Continuation Analysis of Honeypot Camera Traffic Edimax IC-7113W
What do we know about Quasar RAT? A review.
IoT Honeypot Traffic Analysis Series. Analysis of Edimax IC-7113W
BlackHoodie Bootcamp #4 Wrap Up - Berlin 2018
his year we were lucky to be able to attend the 4th edition of the BlackHoodie Bootcamp in Berlin. BlackHoodie is a women-only reverse engineering [intensive] bootcamp, meant to introduce attendees to reverse engineering and other highly technical areas of information security in an intensive weekend. Born in 2015 with only 15 attendees, BlackHoodie has grown now to over 90 participants from all over the world.
Live Class Machine Learning for Network Security
This is the training class “Machine Learning para Seguridad en Redes y Detección de Malware” for the CACIC 2018 Conference.
The live video of the class will be added here soon.
Creating "Too much noise" in DEFCON AI village CTF challenge
During DEFCON 26 the AI village hosted a jeopardy style CTF with challenges related to AI/ML and security. I thought it would be fun to create a challenge for that and I had an idea that revolved around Denoising Autoencoders (DA). The challenge was named “Too much noise” but unfortunately it was not solved by anyone during the CTF. In this blog I would like to present the idea behind it and how one could go about and solve it.
What do we know about NanoCore RAT? A review.
NotPink: The first security conference given by women in Argentina
Notpink es la primer conferencia con charlas técnicas sobre seguridad dadas sólo por mujeres en Argentina. Tuvo lugar en la Universidad de Palermo el pasado 24 de Agosto. Asistieron unas 200 personas. Las charlas fueron dadas por once mujeres especialistas de diferentes áreas de la seguridad informática, esto reflejó diversos matices del ámbito de la cyberseguridad (bancario, medicina, legal, etc). Los sponsors de esta primer edición fueron ESET, Infobyte y Eleven Paths.
My first summer school
Last week I had the opportunity to attend the 1st Transylvanian Deep Learning Summer School (TMLSS). It took place in Cluj, Romania and its main focus was Deep Learning and Reinforcement Learning. Here is the link to website that includes the programme and the full list of lecturers. (link)
5 Things I Learned at my First Two Cybersecurity Conferences
Radhika Gupta is a student studying Computer Science at Carnegie Mellon University in Pittsburgh, Pennsylvania, USA. With the Stratosphere team and thanks to the Women in Tech Fund, she was able to attend Hack in Paris and Nuit Du Hack in Paris, France. Here are five things she learned after attending these conferences!
RESET 2018 Conference Wrap-Up
The first edition of RESET cybersecurity conference took place last week in the Kennedy Lecture Theatre of the UCL in London. Hundreds of attendees gathered together to discuss about cyber attacks, threat actors, threat hunting, defence strategies, and more. The event schedule consisted of 8 technical talks, 2 panels, and opening and closing notes. The speaker selection was excellent, with the presence of well known figures such as Wendy Nather, Kim Zetter, and Rebekah Brown.
High Level Overview of a Malicious Perl Bot
Visit to the NGO Market 2018: The Stories of Civil Society
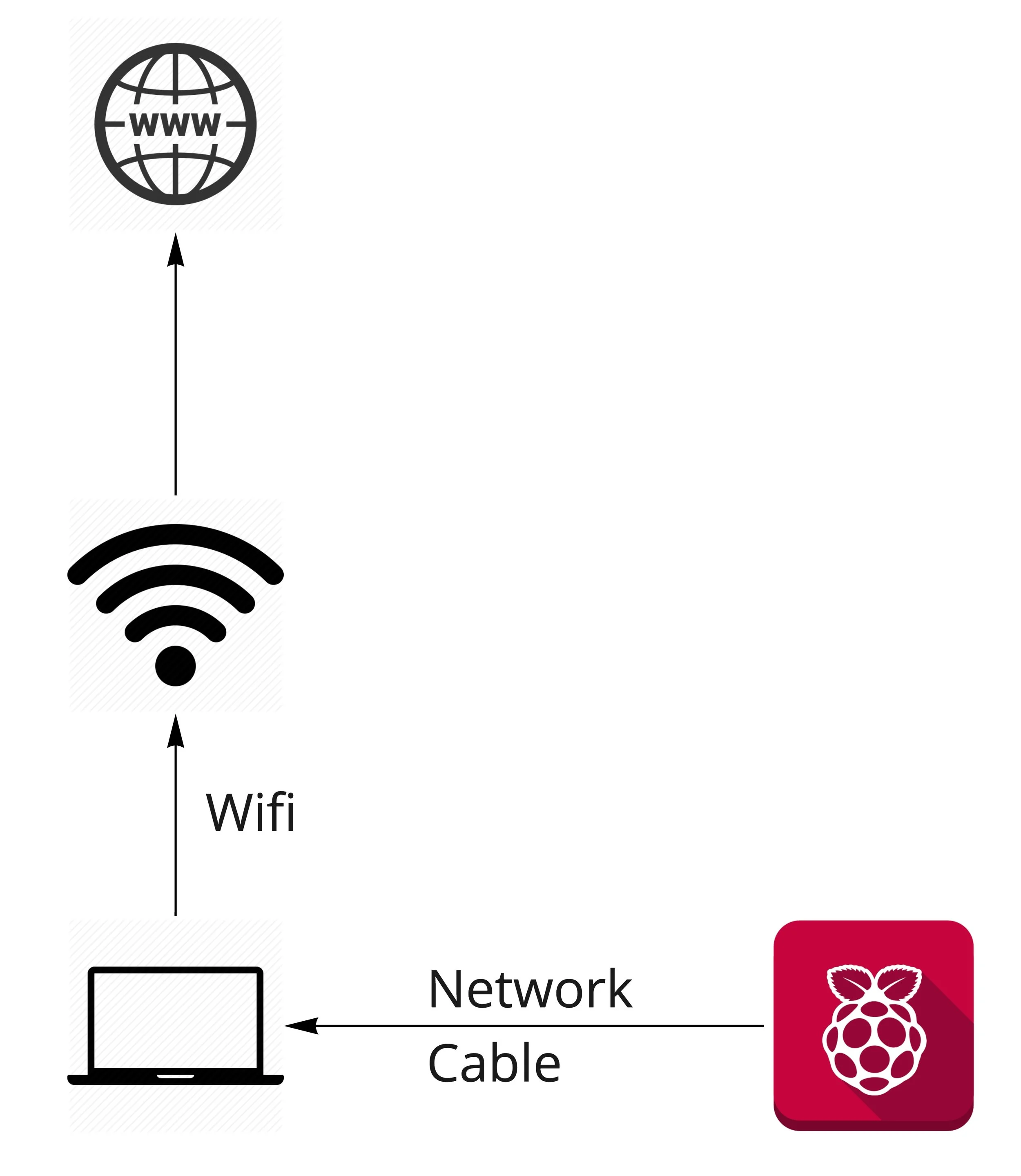
How to Create a Small Lab at Home with a Raspberry Pi to execute Malware
Three Years of Publishing Malware Traffic Datasets
The Stratosphere IPS is a behavioral-based intrusion detection and prevention system. It uses machine learning algorithms to detect malicious behaviors. In order to do that, we create models based on real malware behaviours to ensure a good accuracy and performance of our IPS. For this reason, in 2015 we started our sister project called 'Malware Capture Facility Project'.
Team Learning: Python Introduction for Network Traffic Visualisation
Nomad Project
The goal of the NoMaD project is to collect, label, organize and make available a large, verified and labeled dataset of normal and malicious HTTPS connections. This dataset is designed to support the research team at Cisco Prague as well as to support the research activities and publications of the CVUT University. The project will give Cisco Systems an evolving dataset to generate better and faster analysis; and will give the CTU University the opportunity to research about the HTTPSbehaviors in the network as part of its Stratosphere Project.