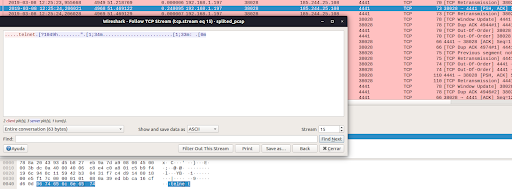
Zeek Package IRC Feature Extractor extends the functionality of Zeek network analysis framework. We create IRC Feature Extractor Zeek Package to automatically recognize IRC communication in a packet capture (pcap) file and to extract features from it. The goal for the feature extraction is to describe an individual IRC communications that occur in the pcap file as accurately as possible.
IoT-23 In Depth: CTU-IoT-Malware-Capture-9-1
A couple of weeks ago, we released the IoT-23 Dataset, the first dataset of malicious and benign IoT network traffic, that consists of 23 scenarios. In this blog post we provide an analysis of Scenario 18, CTU-IoT-Malware-Capture-9-1. This malware sample is Hajime. We analysed the binary sample and the network traffic of this scenario.
Writing a SLIPS Module
In this blogpost, we will walk through the process of developing a new SLIPS module: the VirusTotal (VT) module. This module will listen for new IP addresses and check them against VirusTotal API. VirusTotal returns detailed information on each IP, and the module will process this information and save it to the shared database.
Aposemat IoT-23: A Labeled Dataset With Malicious And Benign IoT Network Traffic
Aposemat IoT Honeypots: 2019 In Review
Introducing Kalipso: the new interactive GUI of the Stratosphere Linux IPS
As the network grows, the possibilities of being infected raise proportionally. One of the most efficient ways to secure yourself is to monitor your own traffic. The Stratosphere Linux IPS and Kalipso are the tools that can help to do it fast and efficiently. In this blog we introduce Kalipso and how to use it to detect malicious behavior in the network traffic.
Attacker IP Prioritizer Program
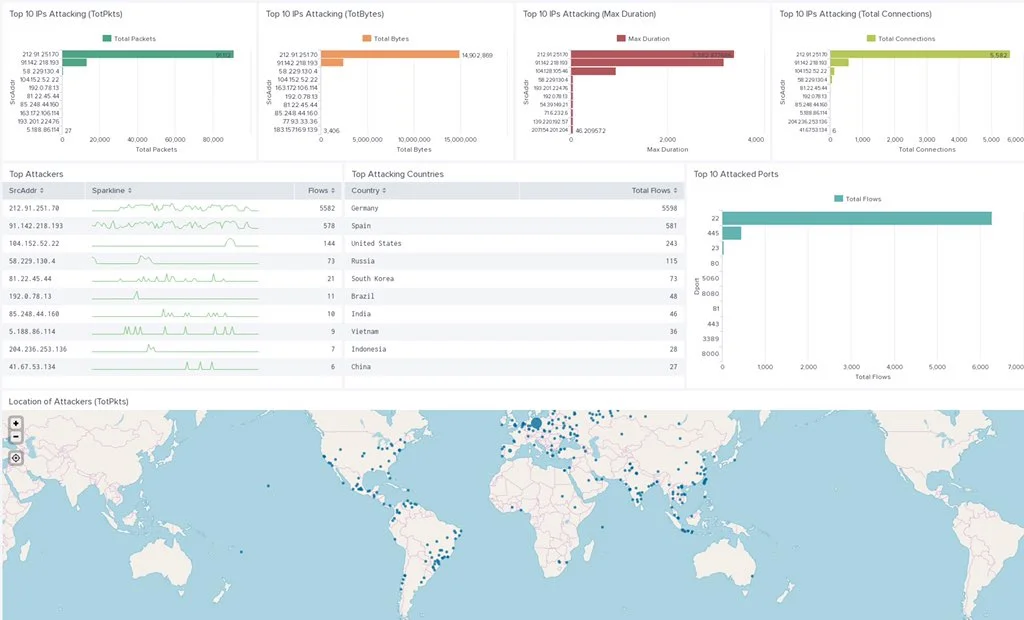
he Attacker IP Prioritization (AIP) algorithm was created in order to sort the huge amount of attacker’s IP addresses to help block them using a blacklist. In the Aposemat project we started a research line called “Polonium in my IoTea” were we are trying to investigate the relationship between organized cyber crime groups (e.g. FancyBear) and their use of IoT devices. In this investigation we needed to analyze thousands of IP addresses attacking our honeypots and quickly decide which ones were the most dangerous.The idea of the AIP algorithm was born from the need to sort the IP addresses of the attackers from a statistical point of view, and then compare those rated IPs to our more technical and in-depth attack research to find out if an IP is really part of an important attacker group or not.
Notes From The Lab: Sudden Increase of Traffic to Port 445
Today @VessOnSecurity tweeted that they have seen an increase on the number of SMB attacks in their honeypot (See Figure 1). We checked our telemetry and indeed we saw an increase on the incoming traffic to our honeypots on port 445. We will describe in this blog post the observations from our telemetry.
Paper: A Study of Machete Cyber Espionage Operations in Latin America
On Wednesday, October 2, at the 29th Virus Bulletin International Conference (VB2019) in London, our researchers Veronica Valeros, Maria Rigaki, Kamila Babayeva and Sebastian Garcia will present the results of more than 3 years of studying and tracking the Machete APT in their talk “A Study of Machete Cyber Espionage Operations in Latin America”.
Hexa Payload Decoder Tool: A Tool To Automatically Extract and Decode Hex Data in C&C Servers
In this blog post we introduce the “Hexa Payload Decoder Tool”, a tool that is able to process a pcap file and return any decoded characters translated to English. This tool was developed to assist the network security analyst when working and interpreting data sent and received by command and control servers used by malware.
Upcoming Talk: Geost botnet. The discovery story of a new Android banking trojan from an OpSec error
On October 2019, Virus Bulletin conference will be held in London. Our researchers Sebastián García, María José Erquiaga and Anna Shirokova will be presenting their research on the novel Geost botnet.
Upcoming Talk: A Study of Machete Cyber Espionage Operations in Latin America
On Wednesday, October 2, at the 29th Virus Bulletin International Conference (VB2019) in London, our researchers Veronica Valeros, Maria Rigaki, Kamila Babayeva and Sebastian Garcia will present the results of more than 3 years of studying and tracking the Machete APT in their talk “A Study of Machete Cyber Espionage Operations in Latin America”.
DEFCON 2019. Beyond Sandboxes. How to Execute IoT Malware and Analyze its Evolution
Project Ludus - Smart Honeypot Manager for Collaborative Defense
In this blogpost we introduce our tool which uses honeypots as a defense mechanism based on the game theoretical model of behavior of the attackers. Ludus fully automates honeypot deployment and management and visualize results in the level of individual routers. [Read more]
IoT Honeypot Traffic Analysis Series. Analysis of Edimax IC-7113W, part 4
In this IoT Honeypot Analysis Series, we focus on the traffic analysis of the Edimax IC-7113W camera. In this episode, we will continue with the analysis of the encrypted packets mentioned in the previous episode. Our goals for this blog post are:
to obtain the AES key from the Edimax server
to understand what happens with the communication after we obtain the AES key
to get a plaintext of the encrypted payload sent from the camera to the server
Summary of the Amparo-CERTUNLP Workshop in Neuquén, Argentina
On May 27-30 I participated as member of the CERTUNLP in a conference organized by the Government of Neuquén province in Argentina. Together with LACNIC in the frame of the Amparo Project we participated giving a workshop to other incident responders and members of CSIRTs. The event was very successful. The audience gathered individuals responsible for the security area of many Argentine provinces as well as National Universities, representatives of local ISPs, banks and other public and private organizations. By Paula Venosa.
First Workshop on Attackers and Cyber-Crime Operations (WACCO) 2019
On June 20th will take place in Stockholm the First Workshop on Attackers and Cyber-Crime Operations (WACCO) as part of the IEEE European Symposium on Security and Privacy (EuroSP). WACCO is a great initiative that provides the opportunity for research, discussions, and sharing on cyber-criminal activities.